Workspace - User and Service Management
Workspace is the evolution of Citrix and Hosted Apps and Desktops Services within Atria.
Workspace is created to help manage and allocate resources at scale to your Clients, via Group Management and executing scripts to manage external systems to Atria.
By using Workspace, you can quickly select and deliver these services, including standing up groups and automations at scale with the click of a button.
In this KB article we will go over the core features, as well as link to more complex features of the service.
Overview
What are the core features?
If you have a new user onboarded, using the Workspace service, you can quickly deliver users with access to resources with a click of a button, across both Microsoft 365 and Active Directory.
Core features are
- Adding a user into a group in Entra ID (Also known as Azure AD, or Microsoft 365)
- Adding users into local Active Directory Security Groups
- Setting TS & RDS Properties against users
- Setup and apply standardised roles to users - ensuring users get the right access for their role.
- Bulk add and change users access.
Additionally, you can run scripts against Customers and Users directly when they are added, for example, if you had a custom script to add NTFS permissions on a user based on their UserName, you can quickly add this script into Workspace to be added against the user when it's setup. Meaning your helpdesk can quickly add users without needing to jump through hoops or run script(s). This is an advanced property of the Workspace service, this is gone into more detail here -
What are the largest changes compared to Citrix / Hosted Apps and Desktops service?
Currently as of writing, you can quickly create a new Private Customer and import through all of their Groups for management within 15 minutes. This means that there isn't a large setup time, or dependencies to setup. This is scheduled to be brought to the Shared environment in the near future.
Functions in detail
Workspace is managed by a few core functions, Lists, Items, ItemTypes, and roles.
List's are the method of providing the Items to clients, ItemTypes are the type of item, Item's are individual resources, and roles are another way to aggregate items together for delivery to clients and resellers.
Below is more information about each of the core functions.
Items
What is a Workspace item?
- Are classified by Workspace Item Type
- Can be Public or Private
- Public - Assigned to multiple Customers
- Private - Can only be seen and used by their designated customer
- Have a Name and description, and can optionally have an icon
- Icons can be Uploaded or you can select an icon reference (You can search for potential icons here - Find Icons with the Perfect Look & Feel | Font Awesome)
- Have a 'Default' (Enable by default) flag
- Inherit settings and configurations by the Item Type
- Have a Groupless flag (Where a identity provided group isn't required)
| Group Type | Definition |
| Private (Direct) | An Item which is created which can only be allocated to a singular customer |
| Shared (Indirect) | An Item which is available to all lists which creates a indirect group assignment |
| Groupless | An Item which does not create a group, and stores the membership of the item logically |
With the above groups, when creating an item, you can additionally select if the item will be Private, Shared or Indirect. These different group types are as follows
Private (Direct Assignment)

Groupless
Create a simple Workspace Item
Lists
What is a List?
- Allow sets of standardised items to be assigned to Resellers
- Each list can optionally be scoped to an Atria Location
- Resellers can be assigned one or more lists
- Group naming conventions and properties can be overridden within a list
- Lists allow grouping of items to suit the service provider
- e.g. Lists could be created focused on verticals, technologies
How are lists allocated?
One thing to note, each customer also has their own 'List' which is Private to the customer. This is hidden via the interface, but these applications are what have been allocated directly to the customer via Workspace Items with the item type of 'Private'. Additionally, customers who are within Private Environments will only see their own Private Items.
Item Types
What is a Workspace Item Type?
- The Identity Provider being used – Out of the box we support Azure AD and Active Directory.
- The group type being used (e.g. Azure AD Security Group, AD Domain Global Group), more details on the difference between the group types below
- A name and description
- A default format for the group name
- Direct or Indirect membership
|
Group Name
|
Description
|
Intended Use
|
| Domain Global Scoped Security Group | - Members can be users, computers, or other groups from the same domain. | - Typically used for granting permissions and access within a single domain. |
| Universal Scoped Security Group | - Members can be users, computers, or other groups from any domain in the forest. | - Useful for granting permissions that need to span multiple domains within the same forest. |
| Domain Local Scoped Security Group | - Members can be users, computers, or other groups from any domain in the same forest. | - Primarily used for assigning permissions within a single domain or for resources in that domain. |
| Azure AD Security Group | - Similar to traditional security groups in Active Directory, used for granting access and permissions. | - Provides security principals access to resources in Azure and other integrated cloud services. |
| Azure AD Distribution Group | - Used for sending emails to a group of recipients without requiring permissions. | - Typically used for distribution lists, mailing lists, or sending notifications. |
| Azure AD Mail-Enabled Security Group | - Combination of a security group and a distribution group. | - Can be used to assign permissions like a security group and receive emails like a distribution group. |
Roles
What is a Workspace Role?
A role contains multiple Workspace Items, when a Role is added to a user, all of the Workspace Items within the role are automatically selected. A similar example to this is a nested group within Active Directory, where one group will give permissions to more nested groups.
Using this, we have an example of a Healthcare client who has many different roles within the business. For example, a Nurse.
- Citrix Access
- Certain File Server Access delivered via Groups
- Access to a Distribution Group within Azure AD
Below is a scribe on how to setup a new role, following this example.
Workspace Ordering
Summary
Workspace ItemType Sample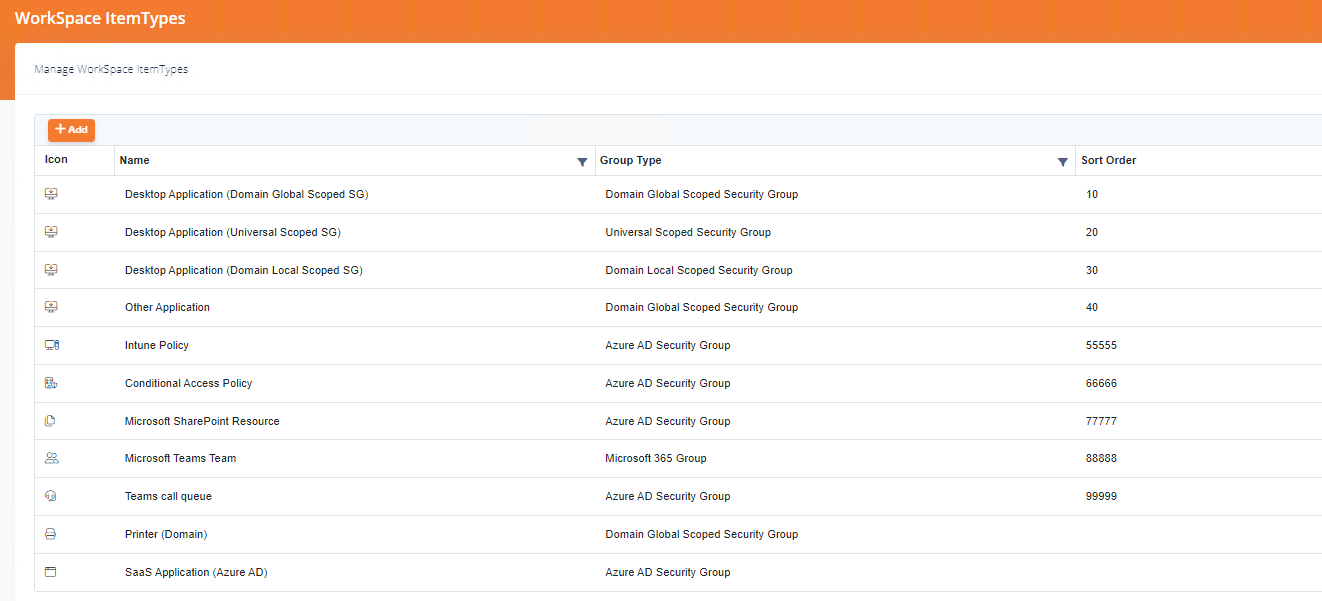
Workspace Items Sample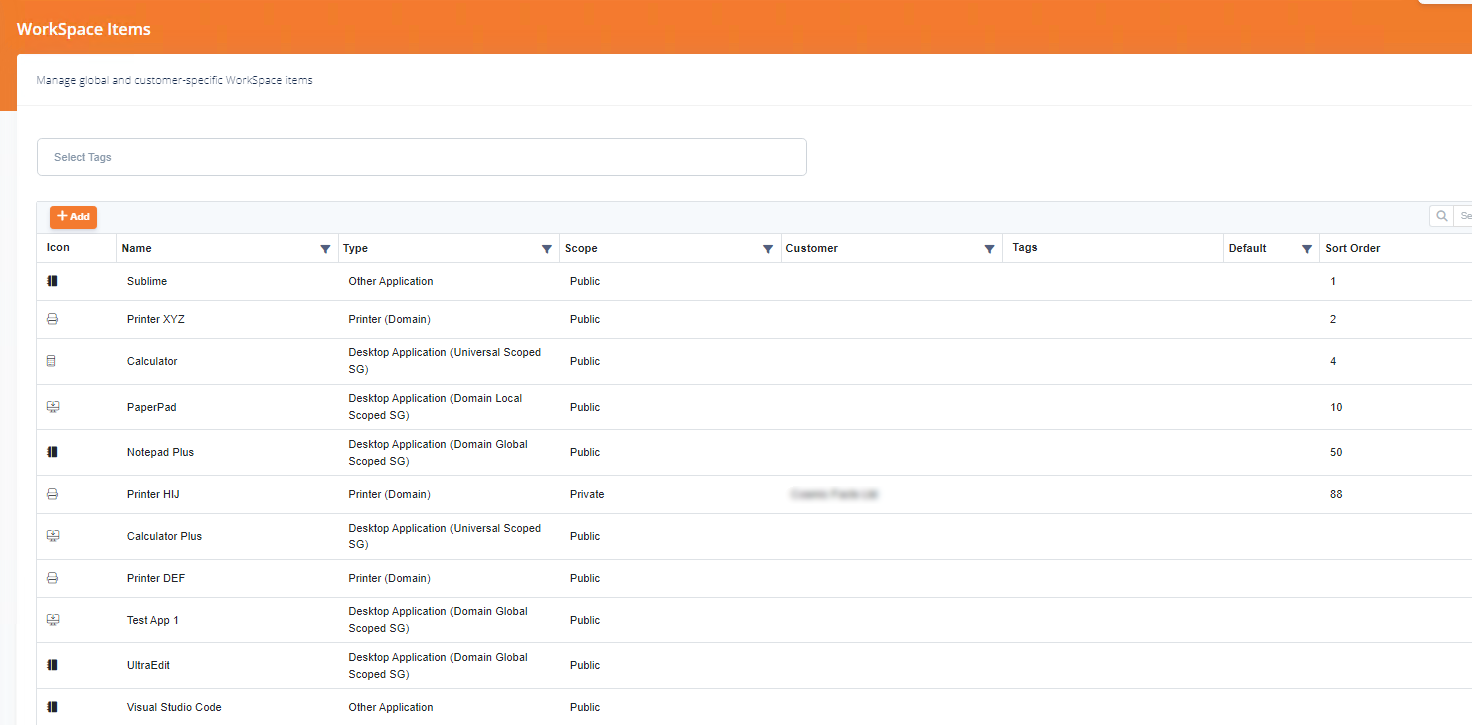
Workspace Role Sample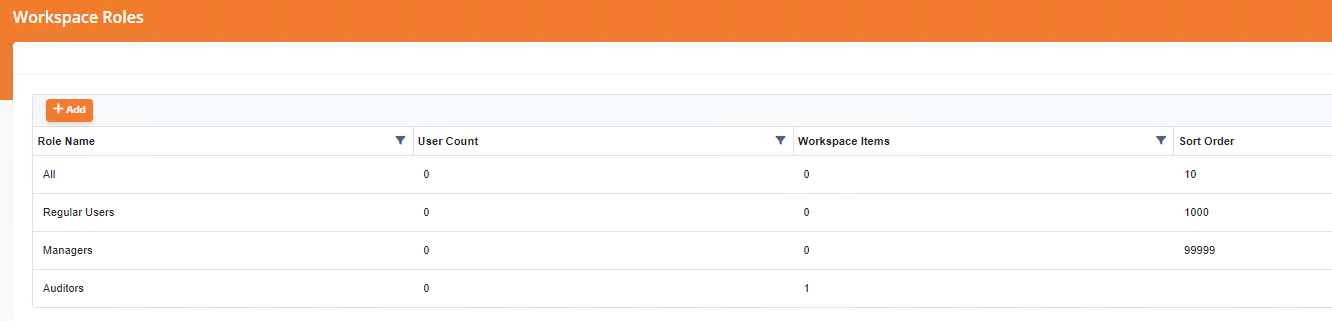
Customer Provisioning Sample
- Order by
- Workspace Item Type SortOrder
- Workspace Item SortOrder,Name
User Provisioning Sample
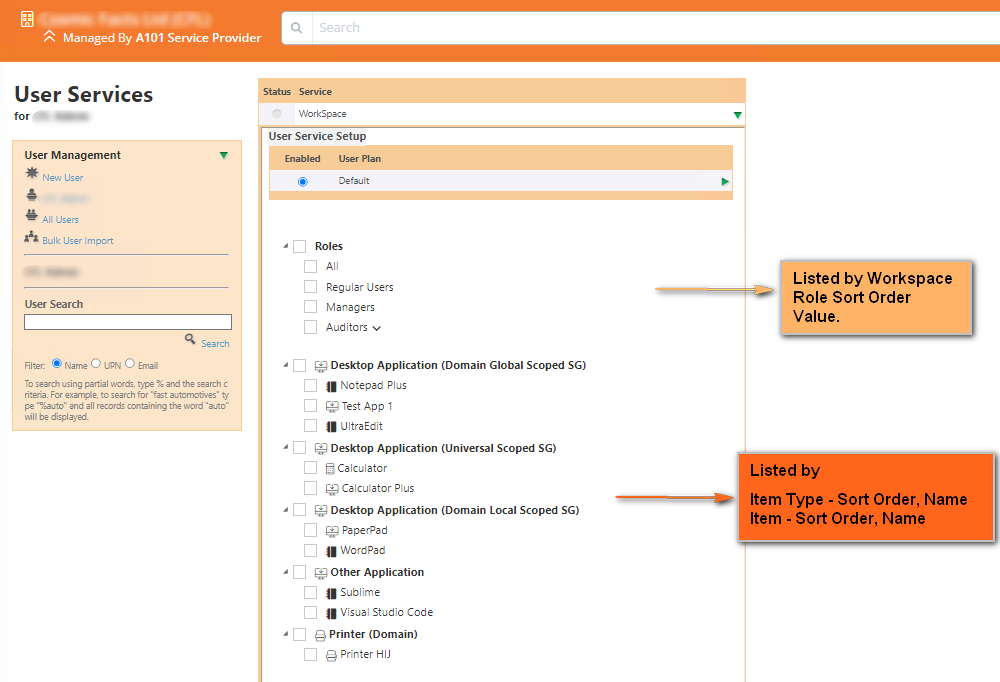
User Provisioning
- Order by
- Workspace Item Type SortOrder
- Workspace Item SortOrder,Name
End User Management
How do I setup user Profile Settings?
Profile Settings are currently configured under the Customer Plan.
Legacy Services that were similar to the WorkSpace Service (Citrix and HostedAppsAndDesktops) both had these settings in different places. Moving them to the Customer Plan configuration means that different plans can be created to target different servers or profile configuration on a customer by customer basis. You'd typically want all users within a Customer to have their Users profiles to be created in the same place, but different customers may be placed on different servers.
How to Configure Terminal Services Profile Settings
You always want to start with "Where do you want the Users Profile and Home folders to be created"?
There are 2 properties that control this, and are referred to as Path Templates:
- Home Drive Path (wsTSHomeDrivePath)
- Profile Path (wsTSProfileTemplate)
These will typically look something like:
E:\ProfileFolders\{CustomersName}\Home\{UserName} or E:\ProfileFolders\{CustomersName}\Profile\{UserName}
or something similar.
Now, these are physical paths on a specific server, and are no good for Terminal Services, therefore a UNC path should really be used that map to these physical paths. So a UNC Path may look like this:
\\ALP-FS01\E$\ProfileFolders\ABC\Home\HarryJ_abc
But this path, even though it points to the correct folder, is not how you will want users to access the path. Users are not Administrators, and cannot access the default Admin shares, nor do you want users to be able to access other customers or even other users' data.
A typical Users Profile or Home share will likely look more like:
\\ALP-FS01\ABC$\Home\HarryJ_abc or \\ALP-FS01\ABC$\Profile\HarryJ_abc
What makes up this path?
- The FileShare Server
- The Share Name (the Customer name or code)
- Whether the Share is Hidden or not ($)
- An optional offset to separate Home and Profile folders
- The User Name
When configuring these values within the WorkSpace Service, some of these properties are actually configured together as a single value. So from a WorkSpace configuration perspective, the values will be:
Note that the Name of the Home drive share and the Name of the profile share are simply the naming convention to use when creating the Share that the users will use to access their data. The dollar($) sign is optional and designates whether the share is hidden or not. Hidden is recommended as it will hide shares belonging to other customers. In a dedicated environment, you might want the share to be visible.
Also, the Path to the Home or Profile shares are physical paths from the perspective of the server they reside on.
The rest of the settings, like Logon Script or whether to connect client drives at logon should be self-explanatory.
The Profile Settings are similar to the Terminal Service Profile Settings
Additional Settings to be aware of
In addition to configuring the appropriate values for creating the correct folders, there are a few settings that control whether these values are set or not. They are
- Enable Profile Management (wsEnableProfileManagement)
If this is set to True, then Profile settings will be configured for users. If set to False, then these settings will be ignored completely.
- Clear User Profile Settings (wsRemoveProfileSettingsOnEmpty)
This setting manages whether settings are deleted or not against the user when the property is blank. This is useful when some settings are managed by GPO, but other settings are managed through Atria. It will allow the setting of values that are populated, and will leave other settings as they are.
How do I change the Workspace Group OU Name?
As of writing, the Group OU is defined by a specific configuration in the Config Service.
Please make sure you have read/write access of the Config Service. If you need assistance of this, please contact our support team.
First, check the current configuration with the below PowerShell command on the Provisioning Server
- Get-AtriaConfig -ConfigKey WSResourceContainer -UseEnvironment
This outputs the default configuration, which is
{
"ActiveDirectory": "WorkSpace Groups",
"ActiveDirectory:Common": "Shared Resources,WorkSpace,Services,CortexSystem"
}
Here we see two specific keys - A 'ActiveDirectory' and 'ActiveDirectory:Common' Key.
These specifically relate to if an item is Private or Shared. The first key without the common is a 'Private' item resource container, the 'Shared' key is for the overall path where resources are stored.
To change this, here are two examples.
Private Items
- Set-AtriaConfig -ConfigKey 'WSResourceContainer' -ConfigValue '{"ActiveDirectory":"Groups","ActiveDirectory:Common":"Shared Resources,WorkSpace,Services,CortexSystem"}' -UseEnvironment
Shared Items
This will be the below command
- Set-AtriaConfig -ConfigKey 'WSResourceContainer' -ConfigValue '{"ActiveDirectory":"Workspace Groups","ActiveDirectory:Common":"Shared Groups, Customers"}' -UseEnvironment
Terminologies
|
Term
|
Definition
|
| iDP Type |
Identity Provider Type, out of the box this is EntraID and Active Directory
|
| Indirect Group | An Indirect Group is created by the Workspace service. For Shared items, we will not put users directly in the root group. Within Active Directory, we will create a group then create a new group as a Member Of per customer. This means that users in different customers are still segregated, but can inherit resources allocated to the group. |
|
Direct Group
|
A Direct Group is a group that is created specifically for one client. This will create a group within Active Directory which Workspace will put users directly into.
|
|
|
|
Related Articles
Importing Active Directory Groups for Management with the Workspace Service
Overview The Workspace service is used to manage access to Application Groups, Applications and Resources for each users. Each Application Group, Application or Resource is mapped to Active Directory security groups. These can then be used with ...Adding a Remote Dedicated Customer
Overview In Atria V15, we now have the ability to manage Private Active Directory's. Customers who have their own AD Infrastructure, gain the same self service and management capabilities of Atria that have worked so well for multi-tenant Active ...Microsoft Online Group Management in Atria
Introduction to Group Management Groups are a fundamental feature used to control access and make information sharing easier. In the Microsoft 365 platform, there are four core group types, all of which have a core component in Azure AD. Many ...Planned Retirement of Hosted Apps and Desktops Service
Overlap between existing Atria service modules Atria has two core service modules used for managing Desktops, Applications and associated Resources. These are known as “Citrix” Service, (CITRIX) and “Hosted Apps and Desktops” Service (HAAD) These ...Job Management (Batch Processes)
Applies to Atria 15 and later Introduction Atria Job management is designed to setup, execute and schedule batch processes. The initial implementation uses this feature to execute PSA integration processes (ConnectWise, Kaseya, AutoTask), you can ...
